The eBay owned popular digital payment and money transfer service, PayPal has been found to be vulnerable to a critical web application vulnerability that could allow an attacker to take control over users' PayPal account with just a click, affecting more than 156 millions PayPal users.
An Egyptian security researcher, Yasser H. Ali has discovered three critical vulnerabilities in PayPal website including CSRF, Auth token bypass and Resetting the security question, which could be used by cybercriminals in the targeted attacks.
Cross-Site Request Forgery (CSRF or XSRF) is a method of attacking a website in which an attacker need to convince the victim to click on a specially crafted HTML exploit page that will make a request to the vulnerable website on their behalf.
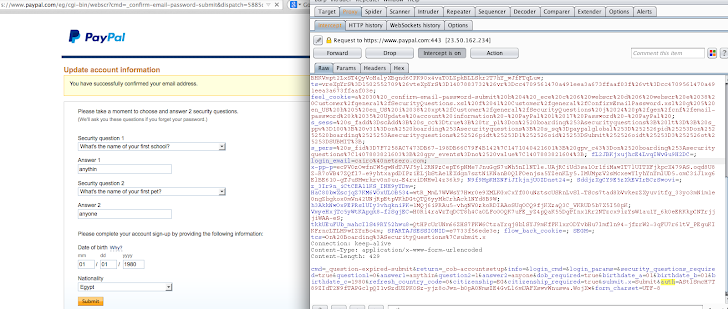
Mr.Yasser demonstrated the vulnerability step-by-step in the Proof-of-Concept (PoC) video using a single exploit that combines all the three vulnerabilities. According to the demo, using Paypal CSRF exploit an attacker is able to secretly associate a new secondary email ID (attacker's email) to the victim's account, and also reset the answers of the security questions from target account.
PayPal uses security Auth tokens for detecting the legitimate requests from the account holder, but Mr. Yasser successfully bypassed it to generate exploit code for targeted attacks, as shown in the video.
Yasser told The Hacker News, "I found out that the CSRF Auth is Reusable for that specific user email address or username, this means If an attacker found any of these CSRF Tokens, He can then make actions in the behave of any logged in user."
Once executed, the exploit will add attacker's email id to victim's account, which could be used to reset the account password using "Forgot Password" option from the Paypal website. But the attacker can not change the victim's password without answering the security questions configured by user while signing up.
Yasser found that another bug in PayPal allows him to reset the security questions and their answers of his choice, hence this facilitates him to bypass the PayPal security feature completely in order to reset the new password for the victim's account.
Paypal security team has patched the vulnerability following the Yasser's report via Bug Bounty Program. Three Month ago, Yasser found similar bug in eBay website that allowed hackers to hijack any eBay account in just 1 minute.
UPDATE
PayPal spokesperson released the following statement:
UPDATE
PayPal spokesperson released the following statement:
"One of our security researchers recently made us aware of a potential way to bypass PayPal's Cross-Site Request Forgery (CSRF) Protection Authorization System when logging onto PayPal.com. Through the PayPal Bug Bounty program, the researcher reported this to us first and our team worked quickly to fix this potential vulnerability before any of our customers were affected by this issue. We proactively work with security researchers to learn about and stay ahead of potential threats because the security of our customers’ accounts is our top concern."
Subscribe to Quick News Updates

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.